Top 20 Linux Network Commands (With Examples)

When managing Linux systems, you will occasionally encounter issues that hinder you from accessing devices and resources on a network. Other times, you will need to retrieve crucial network-related data, such as IP addresses and DNS information, and perform other tasks over the network.
We've compiled a list of the top 20 network command-line tools and utilities that any Linux user or administrator should be familiar with for network troubleshooting and diagnostics. These commands work consistently across most Linux distributions, and you can follow along regardless of your Linux distribution.
Deploy and scale your projects with Cherry Servers' cost-efficient dedicated or virtual servers. Get seamless scaling, hourly pricing, and premium 24/7 support.
#ip command
The ip command is one of the most basic and helpful network commands in Linux.
The command typically displays the status of network interfaces and IP addresses assigned to your system. It succeeds the good old ifconfig command which is now deprecated.
To display the IP addresses on your system, run the command:
ip a
OR
ip addr
 In this example, we have the first interface labeled
In this example, we have the first interface labeled lo, also popularly known as the loopback address or localhost. It always bears the IP of 127.0.0.1 and never deviates from it. It is primarily used for diagnostics.
The second interface ( enp0s3 ) is the system’s physical interface with an IP of
192.169.2.105. Your physical network interface might have a different label, such as eth0`and acquire an IP address based on your LAN’s subnet.
#ping command
The ping command checks the availability of remote hosts by sending an ICMP echo request awaiting a reply. When a remote target receives the request, it acknowledges it and replies by sending back an echo packet.
The command takes the syntax:
ping ip-address or domain
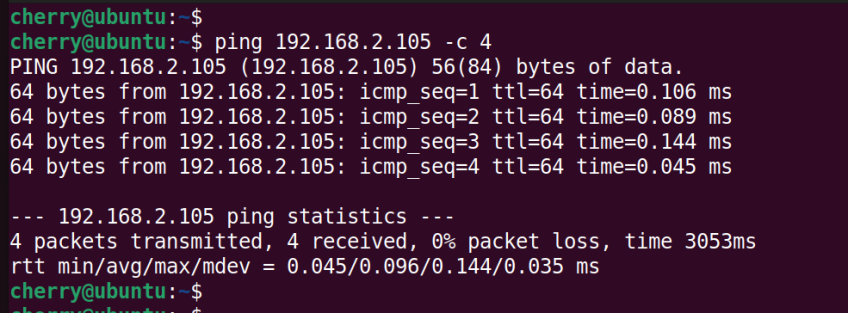
For example:
ping 192.168.2.105 -c 4
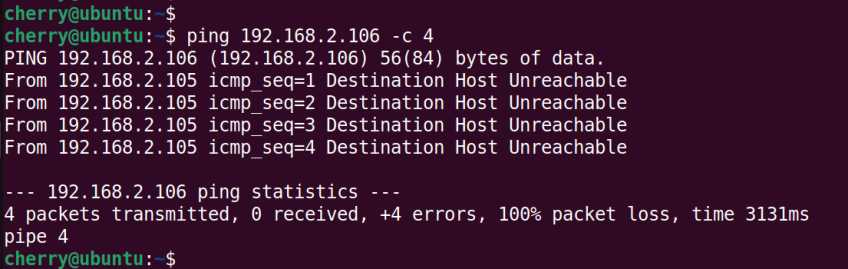
The -c option indicates that we have sent 4 echo packets to the remote node. If the remote host is unavailable, for whatever reason, a Destination Host Unreachable notification will be displayed.
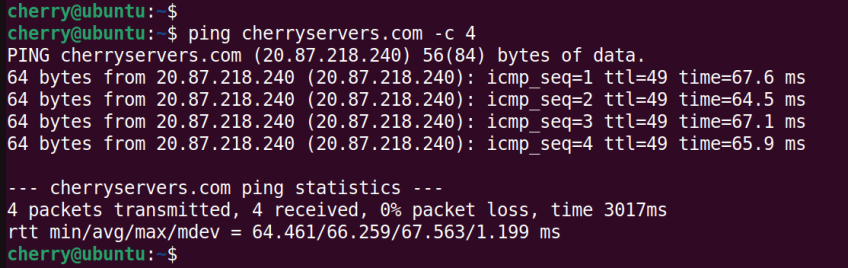
In this example, the ping command tests the availability of a system using its domain name:
ping cherryservers.com -c 4
#hostname command
The hostname command displays the hostname of a server. Without any command-line arguments, it shows your server’s hostname.
hostname
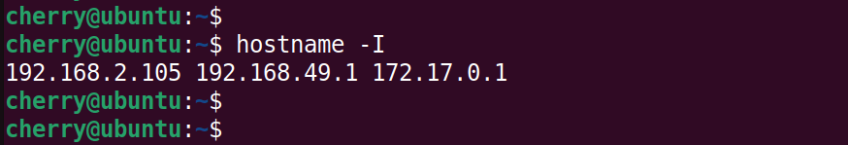
 The
The -I flag, displays the IP addresses of active network interfaces.
hostname -I
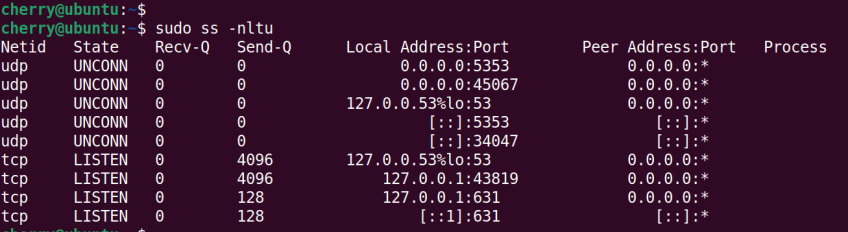
#ss command
An abbreviation for "Socket Statistics", the ss command is a utility that displays UNIX socket connections. The command is an improved version of the old netstat command. It offers valuable insights into open ports, listening TCP and UDP sockets, active connections, routing tables, process statistics, and more.
Here’s an example of the command usage with a few options.
sudo ss -nltu
In this command:
The n option displays numerical addresses.
The l option displays listening sockets.
The t flag includes TCP sockets
The u option includes UDP sockets
Check the man pages for more command-line options and usage.
man ss
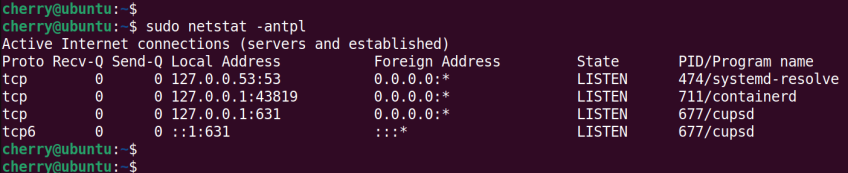
#netstat command
A portmanteau for 'network statistics', the netstat command is a valuable tool for displaying valuable network-related statistics. Although replaced by the ss command, the command-line utility still serves a useful role in displaying listening sockets ( TCP and UDP ) and open ports and port statistics.
The following example displays all listening TCP ports, process name, and their PIDs.
sudo netstat -antpl
In the command syntax:
The a option displays both listening and non-listening sockets
The n displays numerical addresses
The t flag specifies TCP sockets only
The p flag includes the process name and corresponding PIDs
The l flag shows only listening sockets.
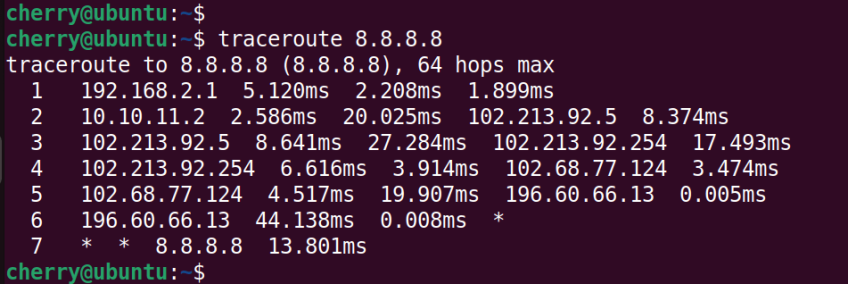
#traceroute command
The traceroute command keenly traces the path taken by data packets as they traverse from one router to another, a sequence known as hops. Loss of packets in a hop indicates that remediation measures should be taken to address packet loss and connection issues.
The traceroute command takes the following syntax.
traceroute ip-address
The following example probes the flow of data packets to Google’s DNS ( 8.8.8.8).
traceroute 8.8.8.8
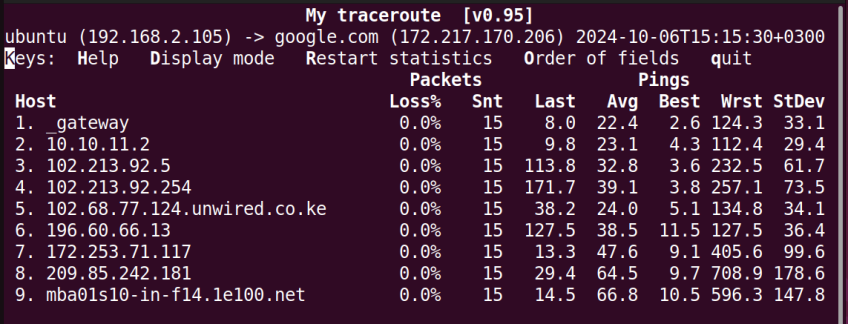
#mtr command
Short for My Traceroute, the mtr command combines the functionality of traceroute and ping. It checks for the accessibility of a host target while also probing the path taken by data packets to the destination.
mtr google.com
#dig command
The dig command is a shorthand for Domain Information Groper. It's a DNS lookup network utility primarily used for verifying and diagnosing DNS issues. The dig command replaces the older nslookup and host commands.
The command can return the following DNS records:
A record: Maps a hostname directly to an IP address.
MX record: Mail Exchange record. Specifies the email server for the domain.
SIG: Signature record for encryption protocols.
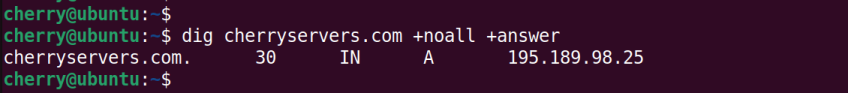
For instance, to perform a DNS lookup for cherrryservers.com, run the command:
dig cherryservers.com
Pay close attention to the ANSWER SECTION.
The first column indicates the domain name of the server The second column is the TTL (Time to Live), in this case 30. The third column indicates the query class. Here, the directive IN is short for the internet. The fourth column shows the query type, in this case, the A record. The last column shows the IP address that maps to the domain name.
 To display the ANSWER section only, run the command:
To display the ANSWER section only, run the command:
dig cherryservers.com +noall +answer
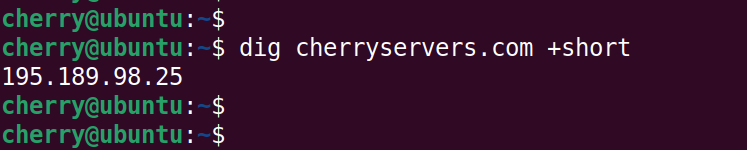
To query the IP address that maps to the domain name and omit other details, use the +short flag.
dig cherryservers.com +short
Notably, the dig command is quite verbose and includes a lot of comments. To reduce the verbosity, include the +nocomments option.
dig cherryservers.com +nocomments
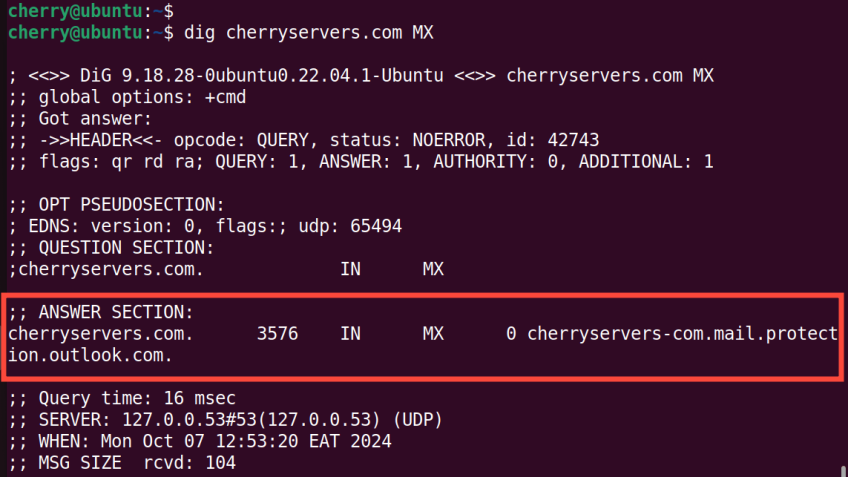
 To query the MX record, use the
To query the MX record, use the MX flag.
dig cherryservers.com MX
#nslookup command
A shorthand for ‘Name Server Lookup, the nslookup is another useful tool for performing DNS lookups. The command probes a DNS server for information such as the IP address, domain name mapping, and other DNS records. Despite being replaced by the dig command, the nslookup utility is a handy network diagnostic tool for troubleshooting DNS-related issues.
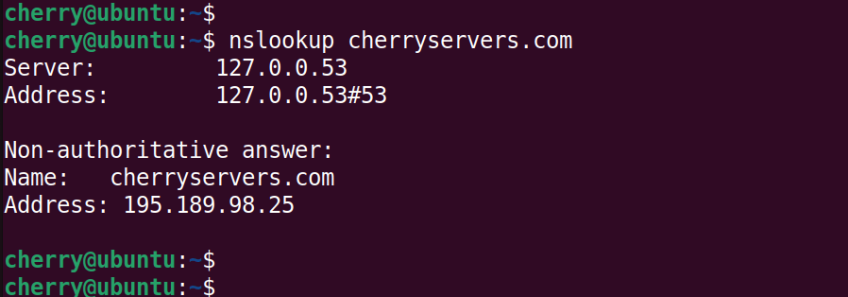
The following command performs a DNS lookup for the domain cherryservers.com.
nslookup cherryservers.com
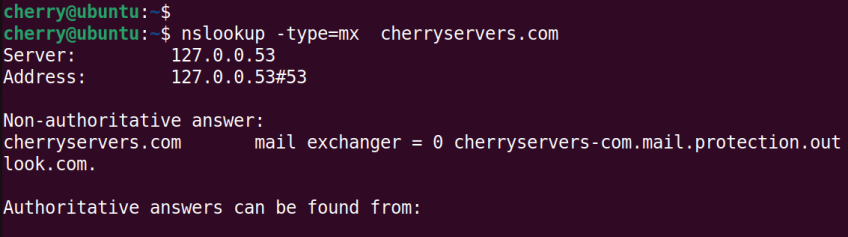
You can specify the type of record using the type= option and specify the record type. For example, to view the MX record for the domain, run the command:
nslookup -type=mx cherryservers.com
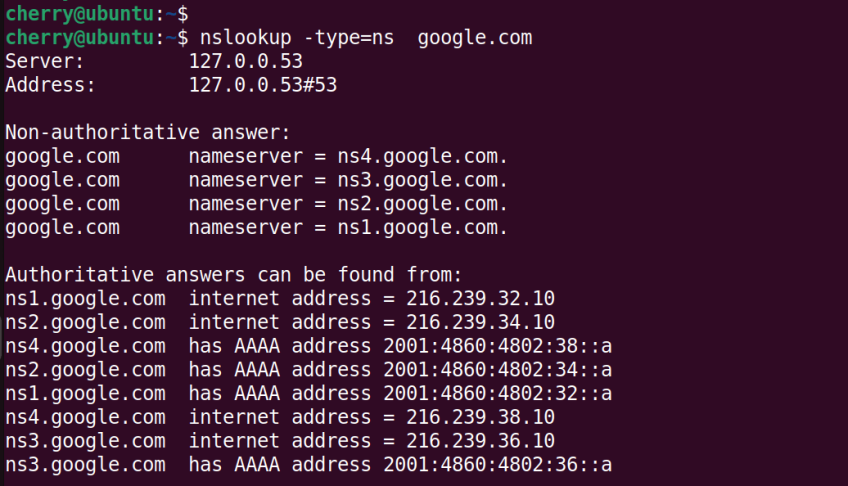
To check the Name Server (ns) records - which maps a domain to a group of nameservers - use the ns argument.
nslookup -type=ns google.com
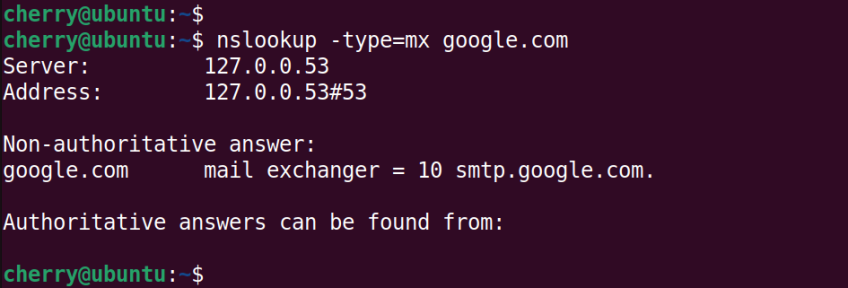
For mail server information, pass the mx argument.
nslookup -type=mx google.com
Also read: Linux shutdown command guide
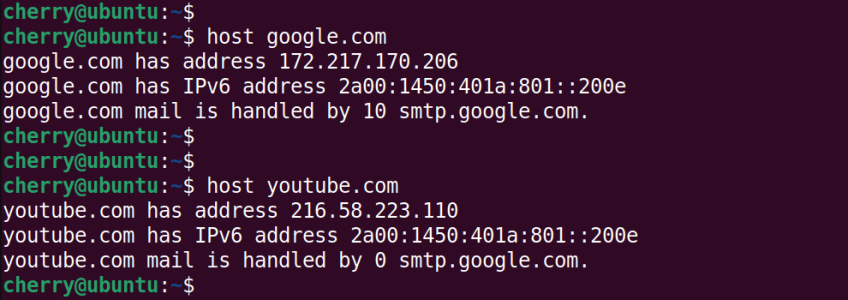
#host command
The host command is a user-friendly DNS lookup tool that displays a domain’s IP and mail server(if one exists). To display a registered domain’s information, simply provide the domain name as the argument as shown.
host domain
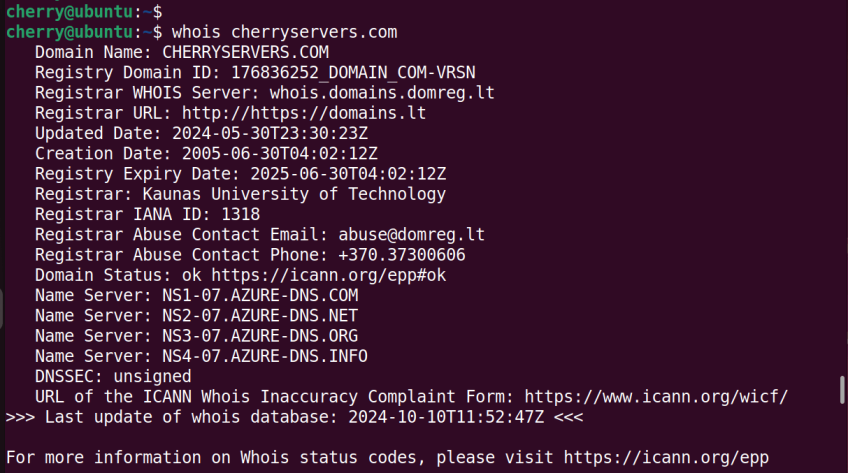
#whois command
The whois command is a protocol for performing domain lookups by querying a distributed database system. The protocol returns information about the domain, such as domain ownership, registration date, business contact information, etc.
To run the command, provide the domain name after the whois directive.
whois domain
#wget command
The wget command downloads files from the internet using the resource's URL. The tool takes the following syntax:
wget [options] [URL]
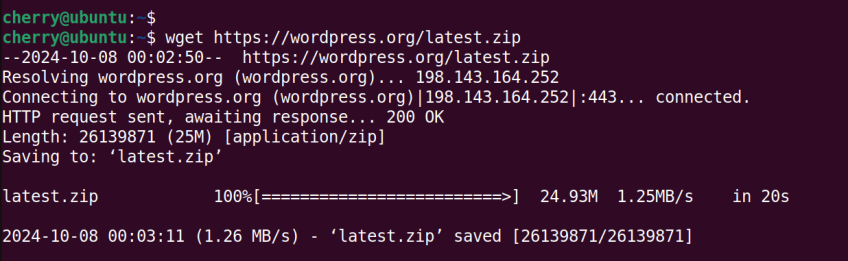
The example shown downloads Wordpress' installation zip file called latest.zip.
wget https://wordpress.org/latest.zip
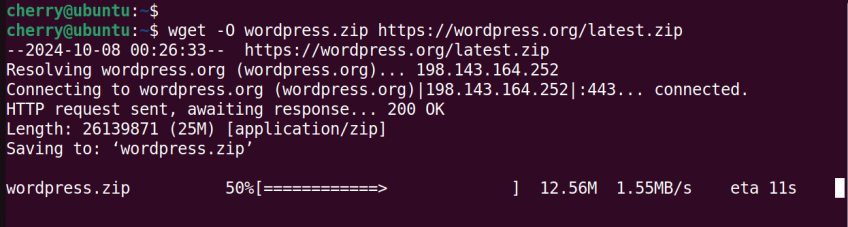
The uppercase -O option saves the file to be downloaded under a different name. Here, we save the file as wordpress.zip.
wget -O wordpress.zip https://wordpress.org/latest.zip
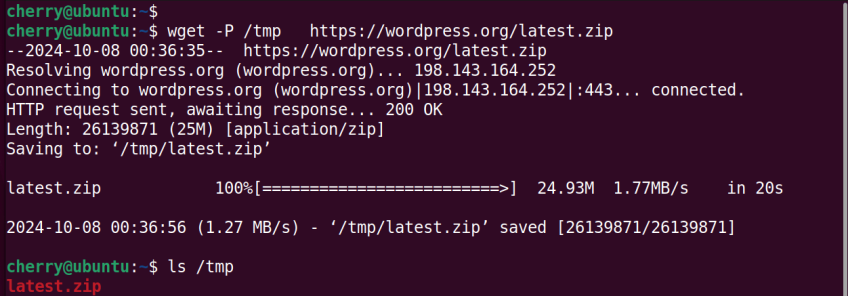
The '- P' option specifies a different directory for saving the file. Here, we save the file in the /tmp folder.
wget -P /tmp https://wordpress.org/latest.zip
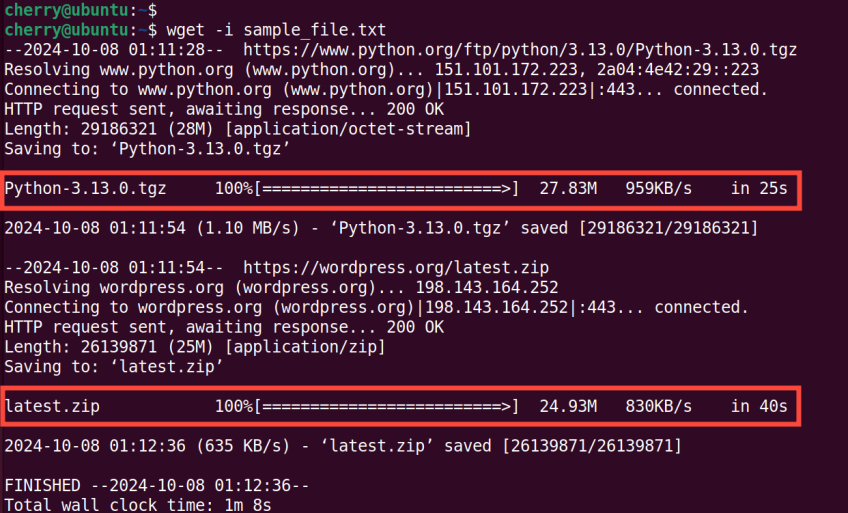
You can download multiple files sequentially by saving file URLs in a text file and passing the -i option to the wget command. In this example, the sample_file.txt file contains the following links.
https://www.python.org/ftp/python/3.13.0/Python-3.13.0.tgz
https://wordpress.org/latest.zip
To download the files, pass the -i option as shown.
wget -i sample_file.txt
#cURL command
cuRL ( client URL ) is a networking CLI tool that transfers data to and from a server or host system by specifying the server’s URL. It supports a range of protocols including HTTP, HTTPS, and FTP.
The command uses the following syntax:
curl [options] [URL]
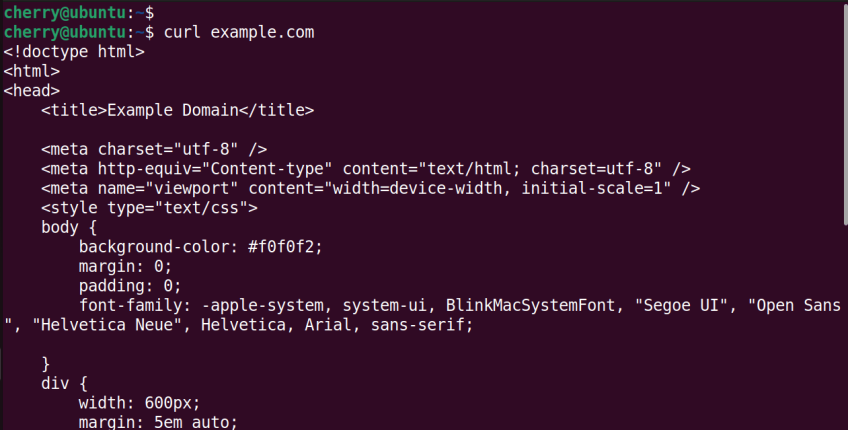
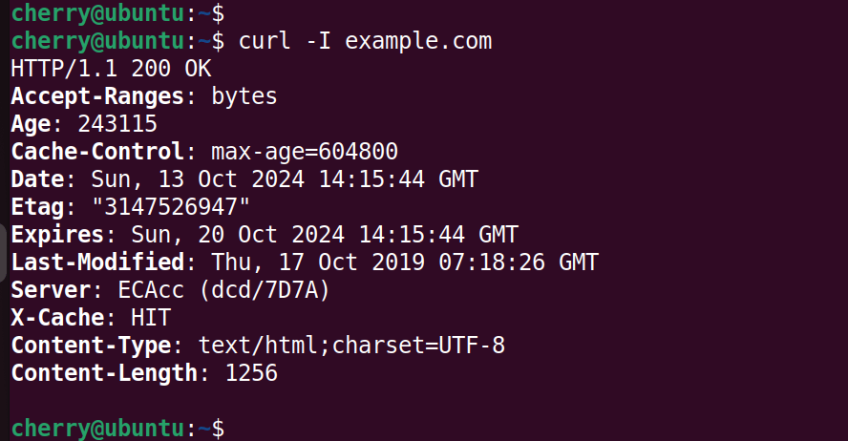
Without any command-line options, the curl command fetches the contents of a webpage. The following command prints the contents of the example.com HTML page to stdout.
curl example.com
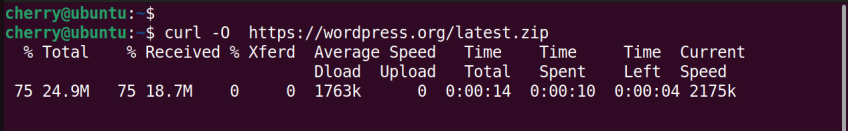
To download a resource, for example, the WordPress compressed file, run the following command. The -O option includes a download progress meter that measures download speed, data transfer rate, total time spent, and remaining download time.
curl -O https://wordpress.org/latest.zip
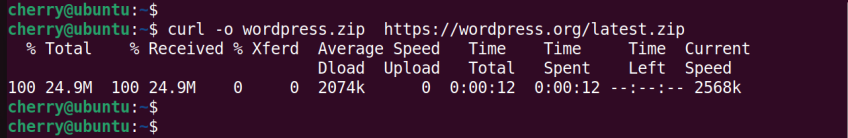
To save the file under a different name pass the lowercase o switch. This example saves the file as wordpress.zip.
curl -o wordpress.zip https://wordpress.org/latest.zip
The I option lets you retrieve the HTTP headers of a file.
#ssh command
The ssh command is used to connect to a remote host securely over a TCP/IP network. The command uses the following syntax:
ssh username@ip- address
Where:
username is the user on the remote host
ip-address represents the IP of the remote host. Additionally, a registered domain name can be provided instead.
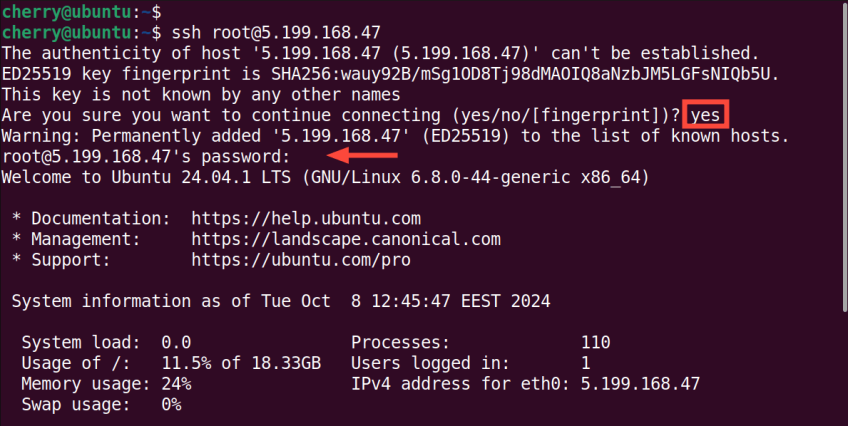
For example:
ssh root@5.199.168.47
By default, SSH listens on port 22. If not the case, the -p flag lets you specify the port number during connection. In this example, SSH on the remote host listens on port 5422. To connect to the host, we will run the command:
ssh -p 5422 root@5.199.168.47
#scp command
The scp ( Secure Copy ) is a command-line tool that leverages SSH’s strong encryption algorithms to copy files securely over a network.
Here’s the syntax:
scp filename username@hostname_or_IP:/remote/path/
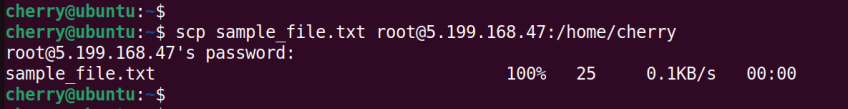
The following command copies a file sample_file.txt to a remote server in the /home/cherry path which is the remote user’s home directory.
scp sample_file.txt root@5.199.168.47:/home/cherry
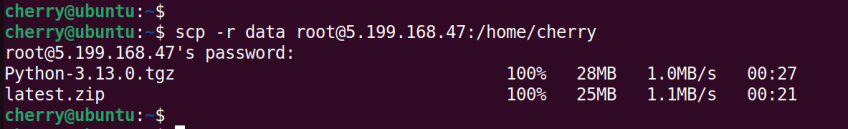
To copy a directory, use the -r for recursive copying. This copies the directory and its entire contents to the remote server. Here, we are copying a directory named data to the remote server.
scp -r data root@5.199.168.47:/home/cherry
Conversely, you can copy files/directories from the remote server to the local system.
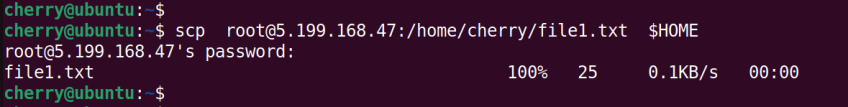
scp username@hostname_or_IP:/remote/file/ /local/path
The command shown copies file1.txt from the remote host to the local machine’s home directory specified by the $HOME environment variable.
scp root@5.199.168.47:/home/cherry/file1.txt $HOME
#Nmap command
Network Mapper, or Nmap for short, is a flexible and open-source utility mainly used for network scanning and reconnaissance. It is used to perform vulnerability assessments on host systems.
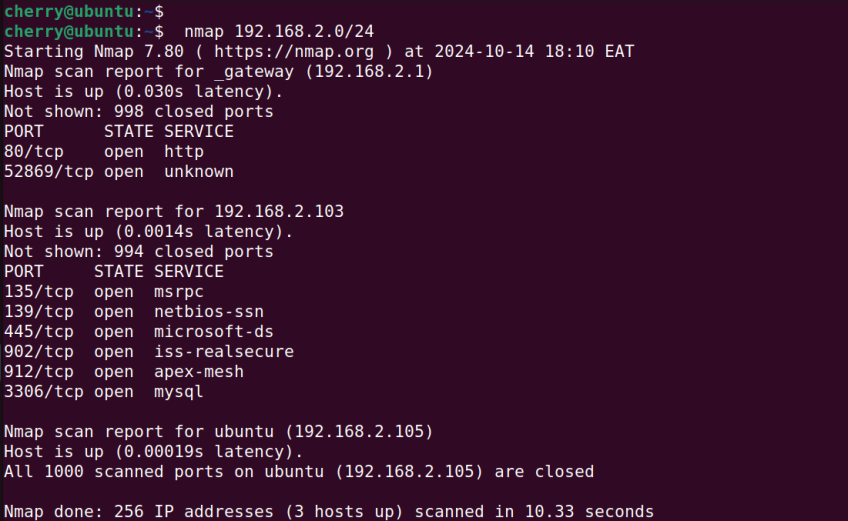
In this example, nmap scans for all the hosts in the 192.168.2.0/24 subnet.
nmap 192.168.2.0/24
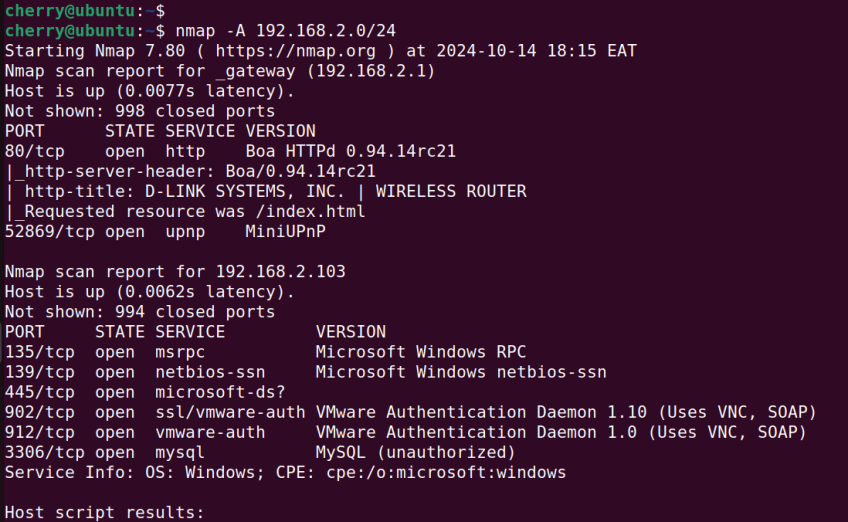
To reveal more detailed or intricate information such as service versions pass the -A switch.
nmap -A 192.168.2.0/24
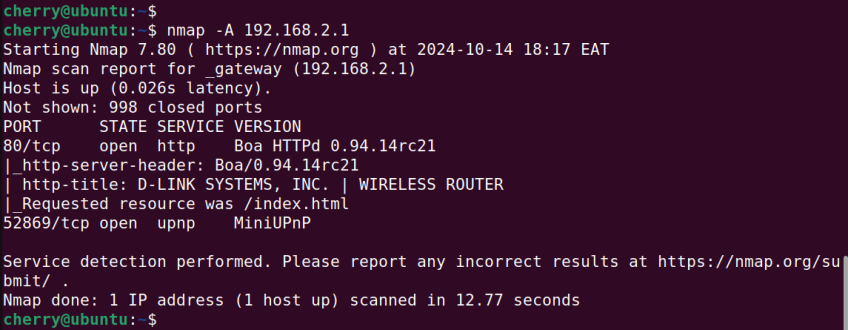
To scan a single host provide its IP address.
nmap -A 192.168.2.1
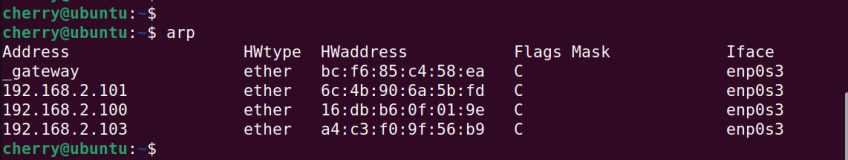
#arp command
The arp command manages the ARP cache on your system. It is used to display or modify ARP cache information. The ARP cache is simply a table that provides a mapping of IP addresses to their MAC addresses in the network. In addition to displaying the entries, you can modify and delete them from the cache.
To display the entries, run:
arp
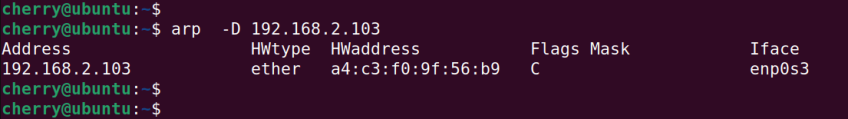
To display the mapping of a single host, pass the -D switch followed by its IP address.
arp -D 192.168.2.103
#nmcli command
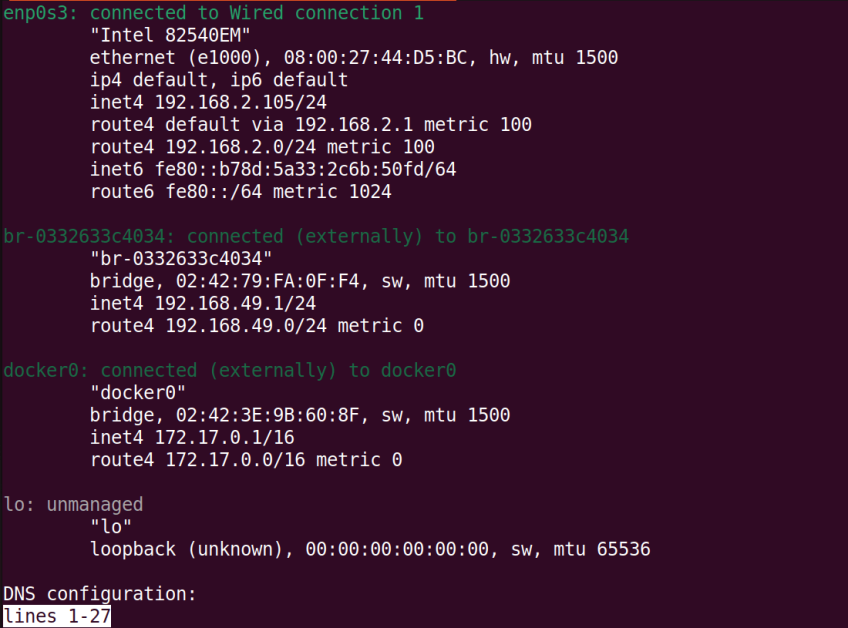
The nmcli is a versatile CLI tool for displaying, modifying activating, and deleting network connections. Without command flags, the nmcli provides a detailed summary of all network interfaces.
nmcli
This provides interface details, including the hardware model, Mac address, MTU, routes, and IP addresses.
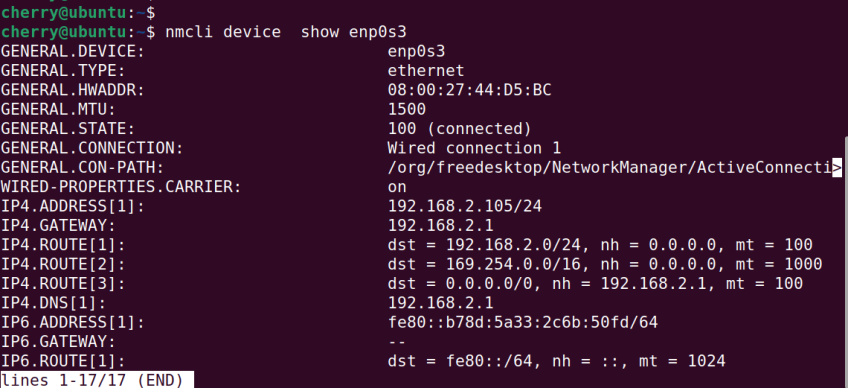
You can display a specific interface connection using the nmcli device show command as shown.
nmcli device show enp0s3
To show the status of all the connections, run:
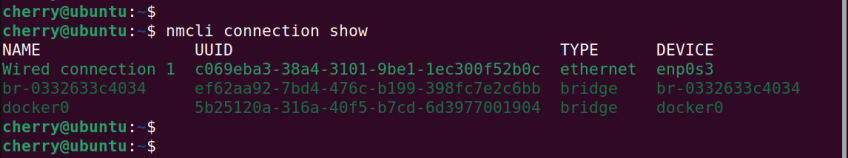
nmcli connection show
#iftop command
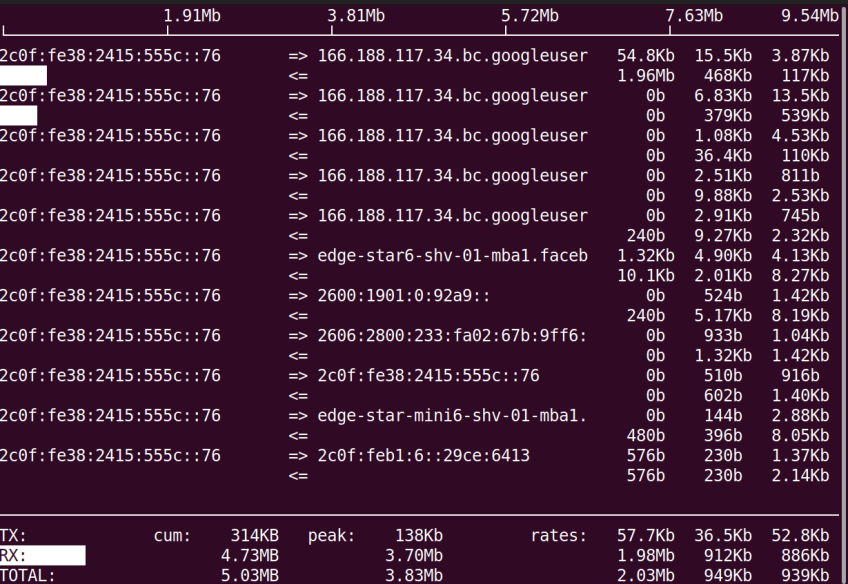
Short for Interface TOP, iftop is a command-line tool for monitoring bandwidth usage on a specific network interface. Run it as a sudo user or root to monitor all traffic flowing through the interface.
By default, iftop is not installed. You can install it by running:
#On Ubuntu / Debian systems
sudo apt install iftop -y
#On RHEL / Fedora
sudo dnf install iftop -y
#bmon command
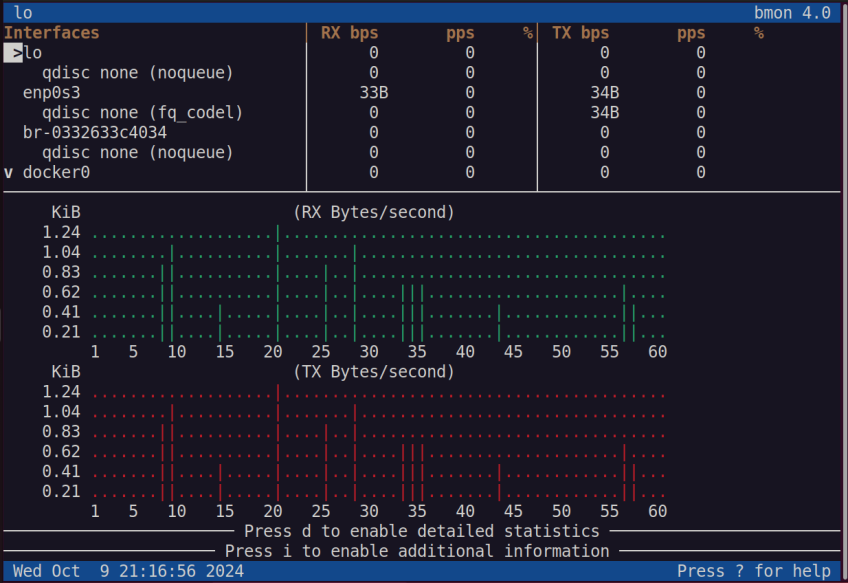
The bmon command is a revamped alternative to iftop. it displays bandwidth statistics in an intuitive and human-readable format.
Bmon is not installed out of the box, and you can do so by running:
#On Ubuntu / Debian systems
sudo apt install bmon -y
#On RHEL / Fedora
sudo dnf install bmon -y
To launch it and start monitoring bandwidth, simply run the command:
bmon
#Conclusion
While not an exhaustive list of all the network commands, this round-up has offered a summary of some nifty commands you can leverage to troubleshoot network faults, monitor bandwidth, and retrieve salient information about network devices and registered domains.
Starting at just $3.24 / month, get virtual servers with top-tier performance.